| OVERVIEW
METHODOLOGY
FAQ's
BUYER's CHECKLIST
ARCHITECTURE
FREE Vulnerability Assessment Click Here Send me a Quote |
|
|
|
User initiates a scan while logged into the web securely
using an SSL-enabled browser.
|
|
|
|
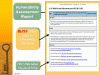
provides reports tailored to each role in your enterprise:
All reports are available securely through an SSL-enabled browser in HTML for convenient viewing and may be downloaded in PDF format for distribution. FREE Vulnerability Assessment Report Click Here is a service of AKABA, Inc.
|
| OVERVIEW METHODOLOGY FAQ's BUYER's CHECKLIST ARCHITECTURE |