|
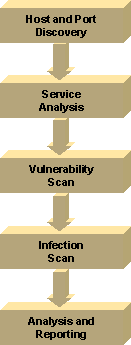
BLISS™ Architecture Designed to meet specific goals. Scalability. The system is designed to handle very large growth in a number of dimensions, specifically growth of customers supported, growth of hosts to be scanned, growth of reach geographically, growth of partners supported, growth of vulnerabilities and infections scanned for. Thoroughness. The system is designed to be as complete as possible in its analysis of the customer’s security. Extensibility. The system is designed to be expandable generally and in a number of specific dimensions: to deliver new types of services, to interface with other systems in new ways and to take on new types of security vulnerabilities. Security. The system is designed to be itself secure, to keep the customers data confidential and to be safe from attack. Accuracy. The system must deliver accurate analysis of the customer’s security. The maximization of True Positives and the minimization of false positives is key. Ease of Use. The system must be easy for a broad range of customers to use to enable expanded market coverage through evolving channels of distribution. There are four main components to the system. Management ModuleThe Management Module interacts with the users and provides all of the management functions inside. Customers change their configurations and receive reports through the Management Module. Partners create Customers, modify their configurations and view status here. Engineers configure new vulnerabilities and infections and provide general maintenance here. Solid access control ensures privacy and security of information. The system has four external interfaces: through an HTTP web interface, through a proprietary Command Line Interface (CLI), through a SOAP/XML interface, and through an interface for use by firewalls for verifying their configuration. The Management Module contains all of the Customer and Partner configuration information for use in the scanning and reporting processes. Central Scanning ConductorThe Central Scanning Conductor is the initiator of all scans. It contains a scheduler that maintains a list of all automatic scans, and triggers the Scanning Engine to initiate them at the appropriate dates and times. The Customer can also trigger it to start an instant scan through the Management Module. The Central Scanning Conductor contains all of the Vulnerability and Infection information. The Scanning Engine pulls vulnerability/infection detection information for use in the actual scans. The Analysis Module pulls vulnerability/infection description and repair information for use in creating customer reports. The engineering team updates the Vulnerability and Infection Databases regularly. Scanning EngineThe Scanning Engine performs the actual security scans. It contains a Meta Scanner that has several sub-modules performing the various types of scans that it provides. When it is triggered to perform a scan, the Scanning Engine performs each of the required scans on the customer network, utilizing the current vulnerability and infection detection information stored in the Central Scanning Conductor. The Scanning Engine can scan hosts directly or through a VPN, enabling secure access to remote hosts. This is particularly important for scanning remote internal hosts of customers. Analysis ModuleThe Analysis Engine takes the raw scan results from the Scanning Engine and processes them using a Security Knowledge Base and previous scanning results from the customer. The Noise Filter reduces false positives. The Trend Module provides trend and differential information. Exception information is provided by the Exception Reporting Module. Scanning ProcessThe system utilizes a five-step process to scan a customer network for security flaws. Host and Port Discovery. During the discovery scan process, the complete customer address range is scanned to discover all hosts (computers) and ports (active services on those computers). This process is also referred to as an inventory. Service Analysis.
Answering ports are analyzed to discover what services are behind them
including version numbers or the previously applied patch history using
custom logic. Vulnerability
Scan. Services are scanned for vulnerabilities (potential
problems). Only relevant scans from service analysis are run. Infection Scan.
Servers and desktops are scanned for signs of existing infections such as
Code Red. Analysis and Reporting.
Information is analyzed against an extensive knowledgebase. Powerful
reports are generated for executives managers and techs.
|
|
PointScan™ provides reports tailored to each role in your enterprise:
All reports are available securely through an SSL-enabled browser in HTML for convenient viewing and may be downloaded in PDF format for distribution. FREE Vulnerability Assessment Click Here |
 OVERVIEW METHODOLOGY FAQ's BUYER's CHECKLIST ARCHITECTURE  |