Spot hazardous files by learning about extensions. Scott Dunn Computer viruses sometimes masquerade as harmless e-mail attachments. The fastest way to spot the interlopers is by their file extension--the letters (usually three) following the final period in the file's name. This extension is an essential aspect of nearly every file on your computer; without it, Windows doesn't know whether to open the file in your word processor or another app, to launch it as a program, or to let other programs use it as a system resource. Knowing a file's extension can also help you customize your system and clean out the dross. Unfortunately, Microsoft started hiding file extensions in Windows 95. To make sure your file extensions are visible, open Windows Explorer or any folder window and choose View, Folder Options or Tools, Folder Options (depending on your version). Click the View tab, make sure the option to 'Hide extensions for known file types' is unchecked (the exact wording will vary depending on your version of Windows; see FIGURE 1), and click OK. Now extensions will be visible for nearly every file on your desktop and in your Explorer and folder windows. The File Types tab in the Folder Options dialog box lists the extensions registered on your system ("registered" means that Windows knows what to do with that type of file; see FIGURE 2). It also shows the file descriptions you would see if you looked in the Type column of Explorer's Details view (choose View, Details). Note that in Windows 9x, you must select one of the registered file types to see its extension displayed in the area below. If you're willing to edit the Registry, you can display most file extensions but hide a few of your choice. Or you can show the extensions of only the file types you select. Here are the file extensions you need to be aware of. An eye on executables: An executable ( Script teasers: Scripts are pieces of human-readable programming code that services translate into machine-code instructions and execute. Windows will launch one of its many script services when you double-click a script file (just as Windows will open Word to display a word processing document if you double-click a .doc file). You encounter scripts frequently while Web browsing and performing other PC tasks, but you probably don't want to let just any old script file run on your computer. The script file extensions to be wary of include those that work with Windows Script Host ( Other service-launching extensions: If you double-click a file whose extension is associated with a Windows service, that service will open and run, using the information in the file you double-clicked to tell the service what to do. Such extensions include Space savers: If you're tired of the screen savers on your system, save disk space by searching for all of your system's .scr files (enter Control Panel icon elimination: Readers frequently ask how to remove icons from their Control Panel window. When the culprit is not one of Windows' own control panels but an uninvited intruder installed by some other program, it's useful to know that most Control Panel icons represent files with the System secrets: Some system file types don't run by themselves and don't open in an application; other programs on your PC use these files to get information about your settings, special programming functions, and other resources. You can customize your system by editing certain One common system file type is the dynamic link library, or Wascally Wegistwy files: Exported portions of the Windows Registry have the
Eliminate XP's Boot Menu
Joe Henriques of Etobicoke, Ontario, reinstalled Microsoft Windows XP Home Edition, but now a menu asks him to choose 'Microsoft Windows XP Home Edition' or 'Microsoft Windows XP Setup' before Windows will start. Since the default option is Setup, he gets an error if he doesn't select XP Home within a short time. The underlying problem: An entry has been added to his boot.ini file, a system file in the root of the start-up drive. Henriques could edit the file to leave only the correct option, but it's easier to tell Windows to ignore the unwanted entry. In Explorer, right-click My Computer and choose Properties. Click Advanced, Settings (under Startup and Recovery). Choose the OS from the 'Default operating system' drop-down list to switch the default. To suppress the menu entirely, uncheck Time to display list of operating systems. Click OK twice.
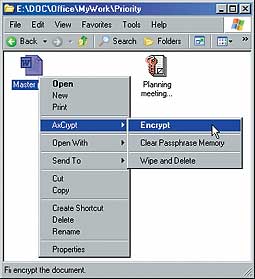
Windows Toolbox: Get Free 128-Bit Encryption for FAT 32 With AxCrypt
To make your files private without resorting to the NTFS file system, look no further than AxCrypt, a handy little utility that lets you lock your files by clicking your right-mouse button. After you install the program, right-click a file and choose AxCrypt to see a submenu of commands for protecting or accessing your files using the utility's 128-bit encryption. Encrypting a folder protects all of the files it contains. You can even have AxCrypt remember a single password and use it by default so you only have to enter it once per log-on and/or reboot. Secure and simple: What's not to like? Though AxCrypt is completely free, its makers encourage a $5 or $10 donation if you like it.
Send Windows-related questions and tips to scott_dunn@pcworld.com. We pay $50 for published items. Click here to view past Windows Tips columns. Scott Dunn is a contributing editor for PC World. |